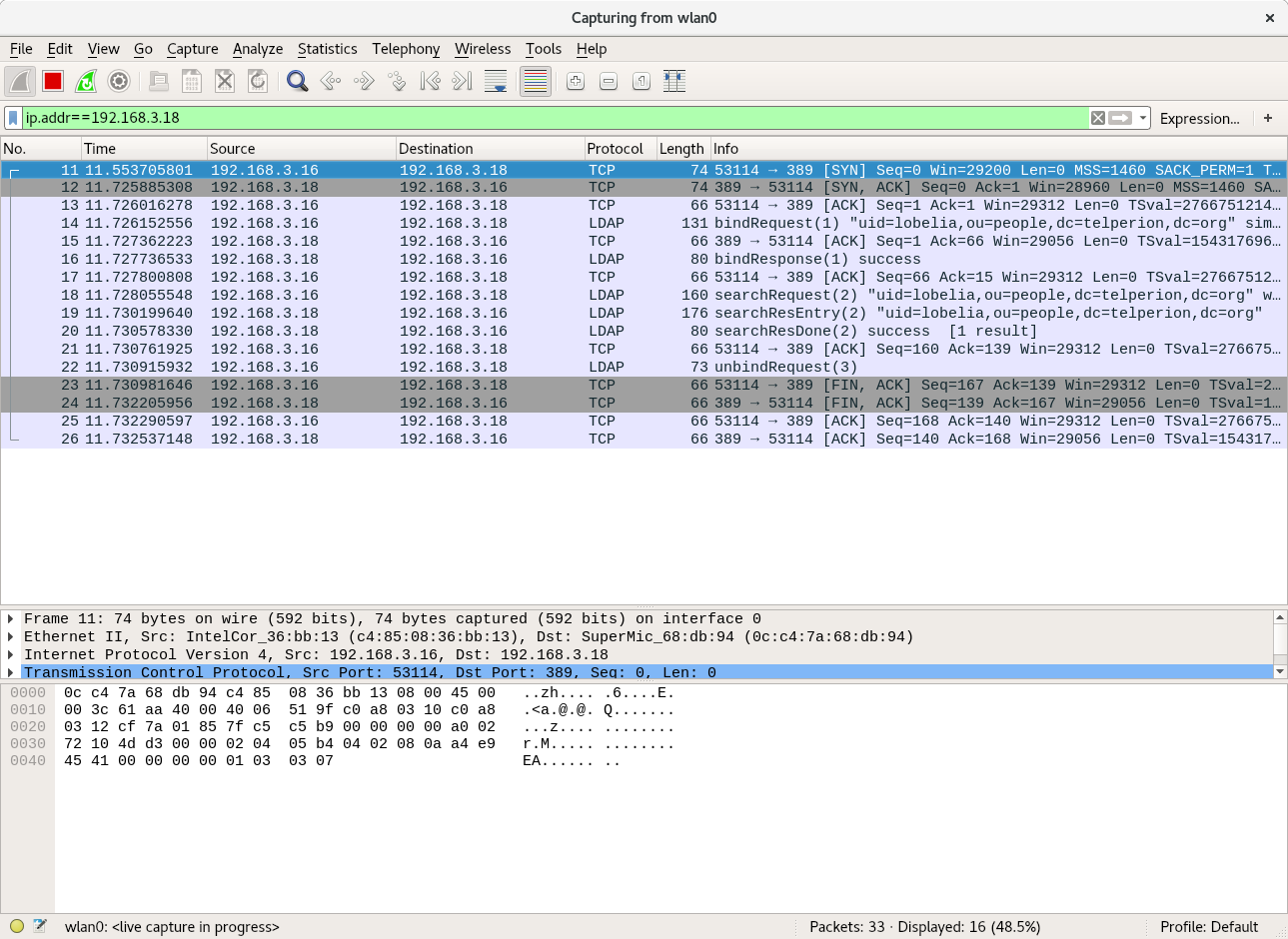
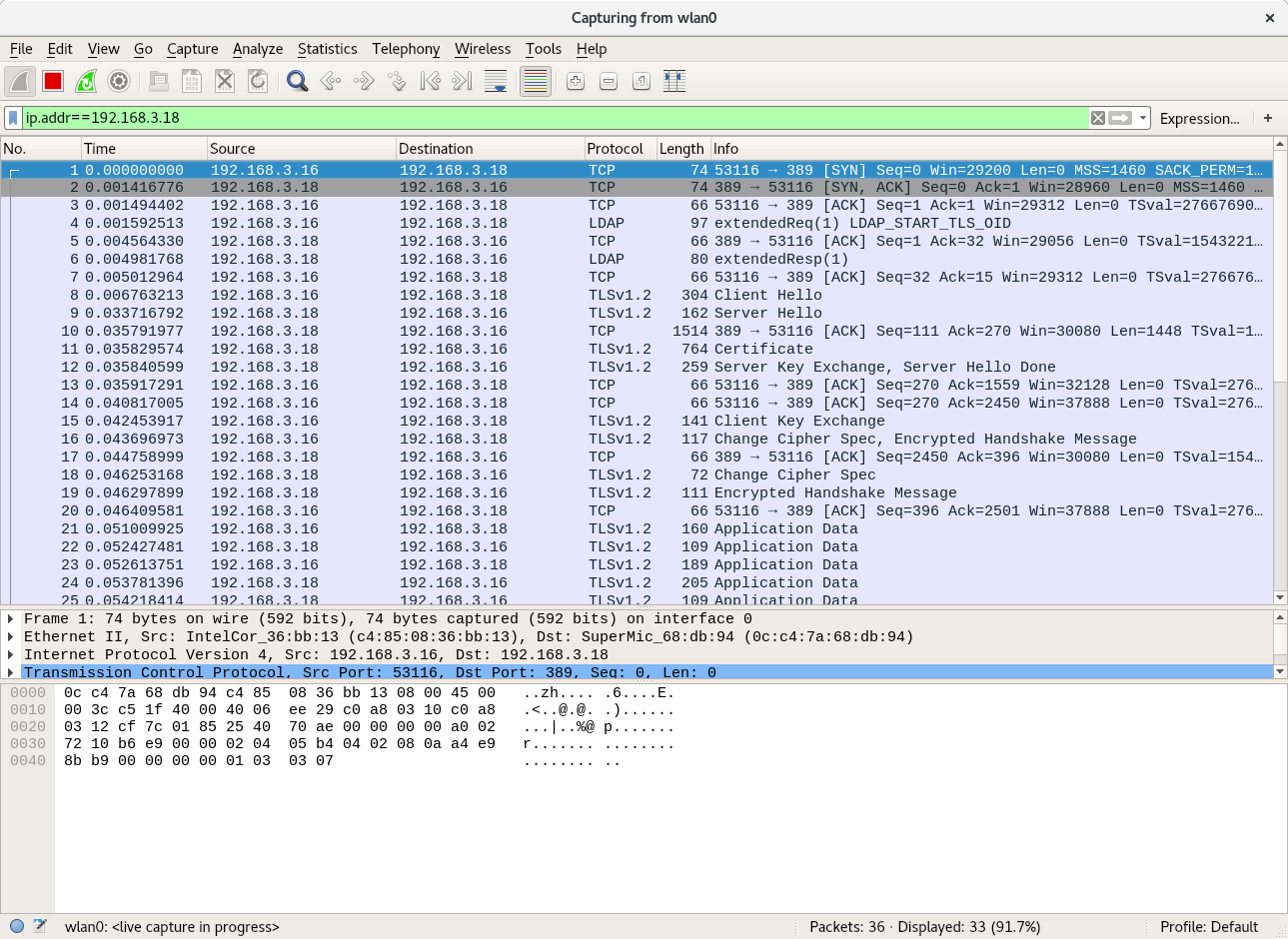
I’ve configured an LDAP database with users, now I need to setup a client(fangorn) to log in. This client is running Ubuntu 17.10.
david@fangorn:~$ lsb_release -a No LSB modules are available. Distributor ID: Ubuntu Description: Ubuntu 17.10 Release: 17.10 Codename: artful
Installing the Client LDAP Modules
Using apt, install the libpam and libnss ldap modules.
apt install libpam-ldapd libnss-ldapd
The debconf prompts the user to enter the nslcd daemon configuration data:
set the ldap server to ldap://barad-dur.telperion.org
set ldap search base to dc=telperion,dc=org
select passwd, group, shadow as services to configure
Configuring the Modules for TLS
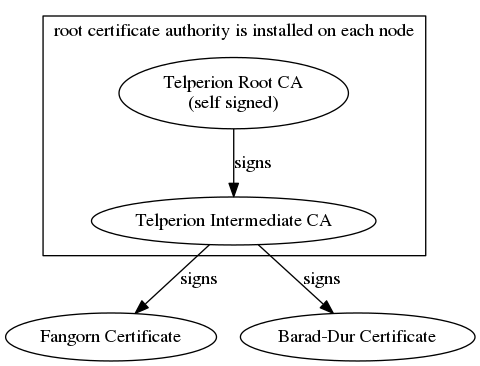
Unfortunately, that isn’t enough, we also need to configure the nslcd daemon for secure tls access. Edit /etc/nslcd.conf to configure. The nslcd.conf manpage has helpful hints for any further configuration.
# The user and group nslcd should run as. uid nslcd gid nslcd # The location at which the LDAP server(s) should be reachable. uri ldap://barad-dur.telperion.org # The search base that will be used for all queries. base dc=telperion,dc=org # The LDAP protocol version to use. ldap_version 3 # force ldap to use start_tls protocol to setup tls connections ssl start_tls # force the tls connection to verify the other end # using a cert signed by the CA tls_reqcert demand # path to pem file containing CA and CA intermediate files tls_cacertfile = /etc/ssl/certs/telperion.org.ca-chain.cert.pem # path to the client certificate tls_certfile = /etc/ssl/certs/fangorn.telperion.org.cert.pem # path to key file containing the private key for the cert tls_key = /etc/ssl/private/fangorn.telperion.org.key.pem # uncomment to enable logging to syslog for debugging issues #log syslog debug
If you experience issues, try adding logging to the nslcd service by adding the following line to /etc/nslcd.conf and restarting nslcd service.
log syslog debug
pam ldap uses the default ldap.conf file located in /etc/ldap. Edit /etc/ldap/ldap.conf to add similar key paths and requirements for verification.
BASE dc=telperion,dc=org URI ldap://barad-dur.telperion.org TLS_CACERT /etc/ssl/certs/telperion.org.ca-chain.cert.pem TLS_CERT /etc/ssl/certs/fangorn.telperion.org.cert.pem TLS_KEY /etc/ssl/private/fangorn.telperion.org.key.pem TLS_REQCERT demand
Make sure permissions are setup correctly on the private keys. The private key should be readable by root and ssl-cert group.
root@fangorn:/etc/ssl/private# ls -l fangorn.telperion.org.key.pem -r--r----- 1 root ssl-cert 288 Feb 17 10:44 fangorn.telperion.org.key.pem
The user nslcd must be added to the ssl-cert group using the command usermod -a -G ssl-cert nslcd, otherwise start_tls will fail.
Also make sure the certs have the correct permissions:
root@fangorn:/etc/ssl/certs# ls -l | grep telperion -r--r--r-- 1 root root 1208 Feb 17 10:44 fangorn.telperion.org.cert.pem -r--r--r-- 1 root root 1836 Feb 17 10:43 fangorn.org.ca-chain.cert.pem
Now that everything is configured, we need to restart the nslcd and nscd services to use the configuration. On ubuntu, run systemctl restart nscd and systemctl restart nslcd.
Testing Configuration
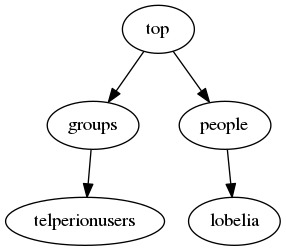
To validate that our configuration is working for nss (using the nslcd daemon installed above), we can use genent passwd to see your ldap users. I recently added a user account for Lobelia Sackville-Baggins as a member of the telperionusers group.
root@fangorn:~# getent passwd | grep lobelia lobelia:x:10000:5000:Lobelia Sackville-Baggins:/home/lobelia:/bin/bash root@fangorn:~# getent group | grep telperionusers telperionusers:*:5000: root@fangorn:~# getent shadow | grep lobelia lobelia:*:::::::0
To get pam working out of the box, I didn’t need to do much. Simply restarting the nscd daemon was all that was required.
Running su -l lobelia with the password, I was able to log in. Lobelia doesn’t yet have a home directory though. We can configure pam to handle some of these setup items for us… another post.